My Bachelor's Degree in Information Security
My thoughts about obtaining a bachelor's degree and my future plans.
At the beginning of this summer, I completed my studies at Russian university in the field of “Information Security” (10.03.01), and received a bachelor’s degree.
In this post, I want to share my experience of going through this stage of life, my thoughts on the need to obtain a higher education degree in 2025, and the available alternatives. At the middle of the post, there will be a short guide to effective learning in IT as one of the alternatives to higher education. At the end of the post, I will share some thoughts on what I will do next.
Disclaimer. Here I want to share my personal experience and vision on this topic, without claiming complete truthfulness or applicability.
I enrolled for higher education in 2021, after passing the selection process based on my Unified State Exam scores. This process began after my graduating from school. I didn’t choose my major by chance — I’ve spent my whole life with computers and wanted to understand how technology works and what I can do with it.
This article is a translation of my article written in Russian. You can find the original one in my Telegram channel if you want.
Education
In short, it’s complete nonsense. This system is designed to train scientists who do research, not specialists who do the work. More details below.
Learning path
The first year is introductory. The goal is to learn how to learn. Subjects: English, mathematics, physics, and computer science. No specialized knowledge is required — just a review of high school material and an introduction to fundamental disciplines such as advanced mathematics.
By “learning how to learn”, I mean instilling a system of knowledge consumption through lectures, awareness through textbooks, and reinforcement through practical assignments. There is a formal division into practical classes and laboratory work, but in reality, these are the same classes. I only encountered a real division into practical/laboratory classes in physics, where practical classes involved solving mathematic problems and laboratory classes involved experiments.
The second year is devoted to fundamental disciplines. The objective is to understand the fundamental components of the world. Subjects include advanced mathematics, electrical engineering, hardware computing, computer networks, and programming. This course provides a comprehensive understanding of the fundamental knowledge upon which practical disciplines are built.
In this course, you need to understand how the things that everything else is built on work. It provides a useful foundation for moving on to practical disciplines, such as logic algebra. Unfortunately, it includes a lot of physics and information theory, which I have never found practical application for in my work in information security.
The third year is an introduction to the profession. The goal is to learn the basics of the main areas of your specialty. Subjects: cryptography, network security, operating systems, legal support for information security, assembler, and technical information security.
Here, students need to be immersed in as many areas of information security as possible. For each discipline, it is important to learn what it is and why it is needed, as well as to immerse oneself in its fundamentals. This helps to determine areas of interest and gain an understanding of the components that make up information security.
Unfortunately, in my case, there was too much emphasis on the compliance part of information security. This includes studying federal laws (FZ), GOST standards, and alike. I do not recommend going to universities associated with regulatory organizations if you are not interested in compliance.
The fourth course is professional. The goal is to start solving real-world problems in your field. Subjects: information security management, secure network architecture, malware, exploiting vulnerabilities, and information security system administration.
Essentially, this is the most interesting course. It’s what I came here for. The classes give you real practical assignments that provide useful work experience. But there’s one problem. No one attends these classes. How can that be?
The problem is that by their fourth year of university, students stop attending classes because almost all of them have already started working. Some in their field of study, some not. As a result, attendance at the most useful classes during the entire course of study is minimal. And, as a consequence, the study of the most useful disciplines for practical work is also minimal.
Elective courses in various fields are also available during the program. Each elective adds approximately 15 classes per semester and allows students to delve deeper into certain topics or learn something new.
I have come to the conclusion that such a program can be used for two purposes: either to pursue a career in science or to broaden one’s horizons. However, it cannot be used for practical (commercial) purposes, as the result knowledge of the individual is mostly theoretical.
I would like to express my special gratitude to the senior students who took on the “Introduction to the Profession” course in my first year of study. They decided to teach students how to participate in CTF, and to participate successfully. The lectures included an introduction to each category of tasks (Web, OSINT, Reverse, etc.), and the practical sessions involved solving these very tasks on the CTFd platform. What you have done is a huge contribution to the development of a large number of future specialists in practical cybersecurity.
People
One of the main advantages of any higher education institution is the opportunity to find a group of people based on your interests. I really wanted this, as I come from a small town where not everyone has heard of computers. And even less had an idea about what you can do with them. I constantly had the thought that my work would be much more interesting in a community of like-minded people.
I was not mistaken in this, because after moving and enrolling, the effectiveness of my studies and work changed significantly for the better. Almost immediately, I had many ideas, and for the first time, I began to see opportunities to implement them. Moreover, this became noticeable even without my own group of friends. Simply being surrounded by a community that is constantly working toward the same goals as you is very motivating to move forward, learn new things, and improve yourself.
But having a community means nothing when you are isolated from it.
What I’m getting at is that studying at university is the best opportunity to find a group of people with similar interests and, most importantly, goals. A group of people with similar interests will give you the opportunity to have fun. It doesn’t really matter whether it’s studying or leisure, it will definitely be more fun in a group.
However, a company with similar goals will make it more likely for you to achieve those goals. The simplest example here is filling in the missing competencies, where one person develops (strong hard skills) and another sells (strong soft skills). The world has seen many examples of such alliances. A more complex example: one person has a great idea but lacks the resources to implement it, and the company fills that gap.
At university, approximately 2-3 months after the start of the academic year, groups of people with similar interests begin to form. During my observations, I identified several types of groups:
- Enjoyers. These guys are all about entertainment. They pay 0% attention to their studies, have no plans for the near future, and live in the moment. In short, they party hard. They are often involved in university social events.
- Passives. Or “going with the flow.” These are people who have not yet decided on their goals in life. They study, but they don’t understand why, they just do it because they have to. They were told to go to kindergarten, school, university, and work, so that’s what they do. They begin to open up somewhere in their third or fourth year, when they realize that they need to start doing something.
- Actives. These are people who understand why they are there. They are focused on their studies and results. But most importantly, they are interested in a particular field or specialty. These guys are constantly busy with something and achieve success in various fields.
- Destructives. These are people who deliberately do bad things. Drugs, gangs, criminals. I recommend avoiding such people by any means and, if necessary, reporting them to all possible authorities. Unfortunately, this really does exist, even in large metropolitan universities.
Here, I advise you to choose a group of people that matches your goals. I don’t want to talk about the importance of moving in the direction of “successful success.” Those who need this path to achieve their goals are the ones who move in the right direction. If your goal is to relax and have fun, a company of serious, results-oriented people will not help you, but will only cause discomfort and demotivation in life.
For myself, I chose a company of active people. Namely, we assembled a team to participate in competitions - HisWoo. In the photo below, we are still very young. We started with the completely clueless “Scr1pt K1dd13s” and grew into specialists in various fields (Red Team/Blue Team). Many thanks to the guys from the team. We have come a long way together and learned a lot. I hope that we will be able to work together again in the future.
Competitions
During my studies, I managed to participate in a large number of information security competitions. I came in both first and last place (mostly first 😎) in various topics in the field. I participated either with a team and solo. The photo below shows my victory in the competition in the “Ethical Hacking” category.
Unfortunately, there weren’t many Red Team events. Most of them were lame CTFs with guessing games that had nothing to do with reality. Recently, attack-defense and red teaming scenarios for infrastructure from vendors have begun to appear, where it was possible to try out various tactics, techniques, and procedures (TTPs).
But in contrast to the meager selection of CTF/pentest competitions at the time of my training, a large number of Blue Team events appeared. In particular, my university began to hold “Cyber Exercises”, where we had to investigate incidents in the infrastructure and write reports on them. Points were awarded for these reports, and teams were ranked according to their scores. The infrastructures were small, with 3-5 hosts available, but this was enough to keep a team of 5 guys busy for 8+ hours. It was difficult at first, especially on Windows hosts, but we got the hang of it and started to get results.
Unfortunately, some competitions had strange selection criteria. Several times, me and my team were refused without explanation the opportunity to participate in competitions where we had to hack something.
I can say with confidence that the competition scene is developing rapidly across the country: interesting CTFs and cyber exercises are appearing, sponsors in the form of leading IT security vendors are coming in, and the tasks are becoming closer and closer to real work.
Diploma
Before graduating, at the end of the fourth year, you have to defeat the final boss — write and defend your thesis in front of a committee. For a bachelor’s degree, this is a semi-scientific work — you have to solve some engineering problem, describe the solution process, and evaluate the results. This greatly facilitates the work, as there are no requirements for “scientific scientificity”, research complexity, or reviews from other scientists, as in a master’s degree graduation.
I chose the following topic: “Development of a software solution for detecting abnormal user behavior based on desktop screenshot analysis.” In reality, it is a web service for processing desktop screenshots using a pre-trained AI model. An agent on the host collects screenshots, the server receives them and sends them to the model for processing. The results are displayed in the admin panel, which shows if there are hits or no hits.
Initially, I thought of doing something related to penetration testing, but the rapid development of AI technologies led me to think that I could use my work on the thesis to better understand how to work with neural networks. It was interesting to try training the model by myself and putting it to work.
The thesis consists of several components:
- Thesis. This is our work in text form. Title page, table of contents, body of the thesis, and list of sources used;
- Appendix to the thesis. This is a “description” of the thesis. Abstract, schedule, thesis assignment, supervisor’s review, and signatures;
- Presentation. A presentation is prepared based on the thesis. It should provide a step-by-step description of the performed work;
- Speech. A speech should be prepared for the presentation. In fact, the presentation must be presented.
The work on all components of the diploma is highly formalized. There is a long list of requirements for each of them. I will not copy the detailed list here, but will only go over the main points:
- Requirements for the amount of material. No less than N pages of text, excluding the appendix. The result for that is 10 pages of work and 50 pages of filler text.
- Formatting requirements. Each element of the text must be formatted in accordance with the requirements. A good kick to learn how to use styles in Word.
- Requirements for a physical copy of the thesis. It must be printed correctly, signed correctly, and packaged correctly.
- Requirements for the duration of the presentation. It must be strictly within 7 minutes. Therefore, you cannot stumble, you need to be familiar with your work and the theory behind it.
- Requirements for answering questions. Dear colleagues from the State Examination Commission (GEK) are essentially obliged to ask at least some questions about your work. And you are obliged to answer at least something.
In fact, the requirements are reasonable (except for the amount of material). It is enough to read them thoroughly once and then not go beyond these limits. There is nothing to be afraid of.
The defense went surprisingly smoothly. I came out, handed out a physical copy of the presentation, gave my speech, answered questions, and sat back down. It flew by unnoticed.
I was afraid that they would start picking apart my decision. Questions like, “Tell us what this part of the code does,” or requests to run it and show how it works in real time. Of course, I was confident in my work, but I was clearly not ready for that. As it turned out, I was completely wrong. During the thesis defense, the commission members can only look at your thesis text, your presentation, and your speech. There is no question of any real-time technical presentation.
I want to thank Sasha, my research advisor, for taking me into his thesis group and helping me implement the project, write my thesis, and prepare for the defense. I would also like to thank Anna, the secretary of the State Examination Commission, who essentially created a guide for passing the thesis, which helped me avoid many hidden problems.
The result is a diploma with honors. My average grade (GPA) for the entire period of study is 5.0. It turned out beautifully. But there is absolutely no benefit in this. So, I made my parents happy, and that’s good.
At the end, you receive the diploma itself (in the first photo of the post) and an appendix to the diploma with the curriculum and grades for each subject. There are no digital copies or certificates signed with an electronic signature.
For a small fee, you can request a European Diploma Supplement. This is also a physical document that allows you to use your diploma when communicating with foreign employers. Let’s say that your Russian diploma becomes recognized in the rest of the world. In reality, it looks like a translation of your diploma supplement into English, plus a couple of pages explaining that your university really does provide higher education.
Job
I decided for myself that after my first year, I would get a job/internship as a penetration tester, no matter what. How? Who knows. I had to do something.
I’ll say right away that the university didn’t help. During my first year, I didn’t gain any knowledge that would help me get a job. Because of this, I threw myself into researching how to get the job I wanted.
I decided to absorb a huge amount of information from free courses and lab work. At that time, these were TryHackMe as a source of theory and HackTheBox as a source of practice. I solved 150 rooms on THM, many machines on HTB, read books, and formed basic intern knowledge:
- Working with Kali Linux, terminal, current tools;
- Automation with Bash and Python;
- Web vulnerabilities;
- Windows/Linux privilege escalation;
- Basic network attacks, arp spoofing, MitM;
- Hacking my neighbor’s Wi-Fi on WPA/WPA2 and WPS.
At some point, I realized that something was missing. Some kind of self-presentation. Since working as a pentester is also IT-related job, I decided to see how junior developers get hired. Spoiler: the theory of similarity with developers turned out to be absolutely correct. In those videos, everyone said: you need pet projects, you need to show the employer what you can do.
What can I do? Run linpeas.sh? How can I show that?
That’s when I got the idea to start my own blog. It was supposed to be that self-presentation. I decided to start writing about solutions to CTF tasks and machines on HackTheBox, which I was actively working on at the time. Everything was in English, because I’m a cool specialist — I had to show that I know English well. That’s how the blog was born — https://maksimradaev.com (at that time it was https://vflame6.github.io). I still try to post something interesting for me there.
I also made a detailed resume, where I wrote that I hadn’t actually worked yet, but I was oh-so-good at what I could do. Look! — and provided as many links as possible: to my blog and profiles on various platforms.
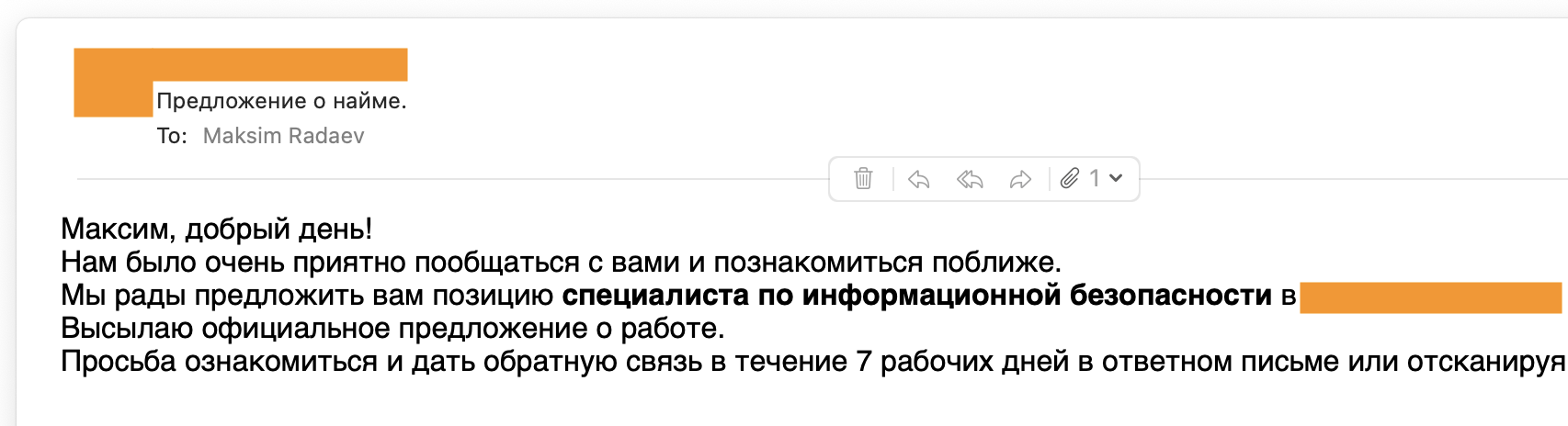
The result: it worked. After my first year, I opened my resume on hh.ru,Russian job-searching platform and applied for all the vacancies that were open. Out of 20 responses, I received 18 rejections and 2 were willing to talk. Of those, I received 1 offer for an internship with the possibility of continuing to work if I passed. Of course, I agreed.
There is my first job offer on the image below:
Next up is work/school/home and career snowballing (I just made that term up).
I won’t talk about the work itself — that’s not the topic of this post. Here, I want to jump to the present and my current position. Now I interview people for various positions in offensive information security field (mainly web/infrastructure), and I’ve had the opportunity to work with various colleagues in the field. And here’s what I can say about higher education:
A university degree really says nothing about a candidate in the current reality of the information security job market. It usually turns out that a candidate with a couple of specialized courses without a degree is much stronger than a candidate with a degree. Why is that?
- Guys with courses understand what they want to do, while guys with diplomas do not, they just want to do something;
- The guys with courses have a lot of practical experience, while the guys with diplomas have a lot of theory;
These two factors are the main ones. There are others, but all of them boil down to these two.
So, any reasons to go to the University?
In this post, I talk a lot about how, in 2025, studying at a university will supposedly be pointless for an information security engineer. This is partly true in terms of technical knowledge and practical skills (hard skills), but completely false when it comes to personal awareness and communication (soft skills). More on that at this section.
University education is definitely necessary in order to:
- Find yourself. You need to understand what you are good at, what you are capable of doing, and what you really want to do in life. Clarity on these questions will provide a foundation for further career and personal development.
- Find people. Namely, a group of people who share your interests. These are essentially the people who are most likely to accompany you throughout your life. The quantity of the group is not important. What really matters is the quality of this group. The better it is, the higher the chances of doing something truly worthwhile within your life.
- Learn to negotiate. Or, more accurately, to communicate. Studying at a university will create a large number of problematic situations, both technical and human. Technical issues are resolved with personal knowledge, human issues are resolved with communication. More specifically, you need to learn to negotiate goals, conditions, and expectations. You also need to maintain constant status updates and feedback.
If you already have all of this, don’t waste your time. If not, be sure to go. In my opinion, the first two courses (years) are enough to cover these three topics. After that, you can confidently enter the job market, spending less and less time at the university.
Dream a little, how this education system could be improved?
As I said above, two years are enough to resolve the main strategic issues: finding yourself, finding people, and learning to negotiate.
The problem remains that the first two years at university are technically useless. By this I mean that the first year is a repetition of the school curriculum, and the second year is fundamental knowledge. There are either no practical tasks or very few of them. What happens in real work is even less likely to be taught. This is where the problem with university education arises.
If I understand correctly, this should have been solved by a system of universities for scientists and colleges for workers. But, unfortunately, in Russia colleges simply repeat the university program in a shortened form.
The solution is two years of training in a specific specialty, a kind of proper specialization program. The goal is to train junior-level specialists who are capable of solving real-world problems. At the end, there is an exam in the form of a project taken from real-world cases. This project should serve as proof of the specialist’s competence.
The program should be designed in accordance with the specialty and future position. For IT, it is necessary to exclude or minimize the study of fundamental knowledge in, for example, physics, and to create the most comprehensive program possible for writing frontend/backend applications, software architecture, networks, and product infrastructure.
Similar developments can already be seen at universities that collaborate with leading IT vendors. Unfortunately, however, most of these programs are master’s degrees. To get there, you need to study the fundamentals for four years. Why? That’s a non-answered question.
Alternatives to University education
Now the question is: what should current students do if they are not studying at universities with cool cybersecurity programs, of which there are only 2-3 in the country? The answer is to look for alternatives and start studying them.
First of all, learn English, everything that is localized is bullshit. All high-quality, unedited information accumulated by humanity is in English. In the current situation, it is essential to know English, at least to be able to read literature and understand its meaning. With this in mind, we reject platforms such as Skillbox, Geekbrains, and others.
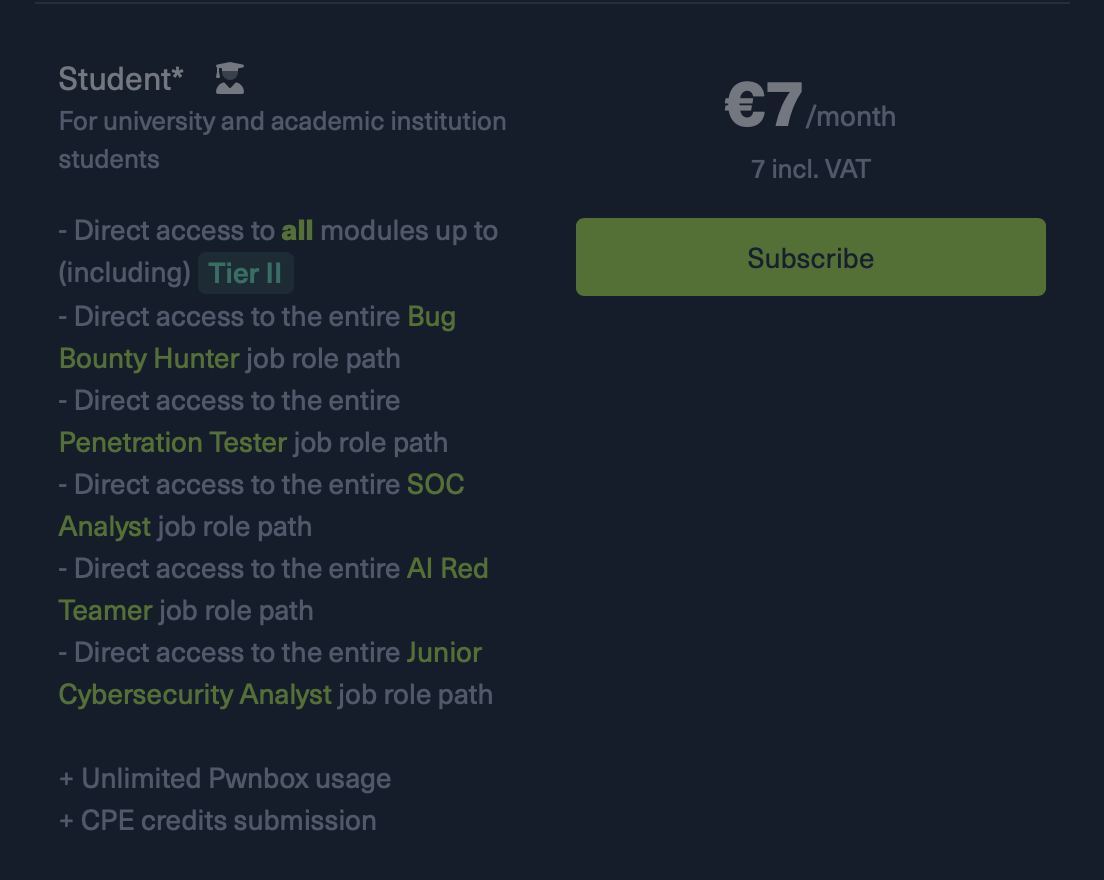
The next question is money. If you don’t have money, take free courses on the subject of your specialty. There are many of them now, and it’s easy to gather basic knowledge from the first links in Google (and now you can try ChatGPT). If you have money, you can take an inexpensive specialized course, for example, pay for a student subscription to HTB Academy, its description is in the screenshot below:
I don’t recommend taking cool courses with certifications. The big problem with this approach is that it’s narrow-minded in terms of money. When knowledge is already prepared and presented to you on a silver platter, there is no need for research. And the “power” lies precisely in the ability to research and find solutions to the tasks at hand.
But that’s all just talk. I’ll try to give some specifics. What should a student read and do, for example, in the field of pentesting, which is what I’m into:
- Free courses. TryHackMe. Let’s start with this one. It has Learning Paths with a fairly good difficulty curve, and every topic has public solutions if something doesn’t work out. Start with the most basic modules on fundamental technologies;
- Source of relevant information. You need to immerse yourself in the subject. Here’s something for everyone: X (Twitter), Telegram channels, Hacker magazine, and a large number of different thematic blogs;
- Books. A lot has already been written on the topic of pentesting. To start with, pick up a general book such as Kali Linux. Penetration Testing and Security, then delve into specific domains of personal interest, such as Pentesting Active Directory and Windows-based Infrastructure;
- Paid courses. HackTheBox. Once you have mastered Jr Penetration Tester on TryHackMe (on your own), you can move on to more complex tasks. The first goal is to solve all available (current) easy and medium machines on HackTheBox;
- Think (and act) further. Until you are confident in your abilities for real work.
It is important to note that it is not necessary to focus on “pentesting” here. Such a system will work for becoming a specialist in any IT field.
I can also recommend reading a blog post - My OSCP Journey, in which I described several important points for preparing for the OSCP exam. In fact, it works and will be useful in any learning process, regardless of the course/exam.
From my own experience, I can say that you can easily master “intern” knowledge using only free sources of information. I only started taking paid courses and certifications a year after I got a job.
All you need is a laptop, an Internet and a silence.
What next?
I have completed one major stage of my life. I have finally become a “full-fledged person” by the standards of the society in which I was born. What will I do next? The answer seems simple—work and live. But I want to give myself more specific answers.
Higher education
Firstly, no more higher education. I went through it in practice and realized that there are more effective and higher-quality methods of learning for my purposes. Therefore, I am not going to pursue a master’s degree — there is no reason for wasting my time.
Neural networks
ChatGPT appeared when I was in my second year of university, working and studying at the same time. I wasn’t ready for “innovations” in my habits, so I missed the initial hype on the topic and started figuring out the chatbot a few months after its launch.
Once I figured it out, it immediately became clear that this thing would change everything. Studying, work, and life in general would be divided into before and after. My approach to writing articles and letters, researching unknown topics, and finding quick solutions to work tasks changed. In essence, I now need fewer skills and less time to solve a larger number of problems than before.
Neural networks are too new a field, one that is increasingly taking over our world. All education systems are unprepared for their impact on the learning process, problem solving, and achieving results at work.
In essence, a neural network is a new calculator. Those who accept and master this new reality will win. If we look back at history, we know about the demand for skills:
- First, people who could remember a lot were in demand. Their value was data storage.
- Then, people who were good at calculating what was recorded were in demand. Their value was data processing.
- Then, people who were good at systematizing what was calculated were in demand. Their value was data systematization.
- Now, people who are good at analyzing systematized data are in demand. Their value lies in making conclusions based on data.
My opinion is that people who manage neural networks will be in demand in the future. Their value lies in making decisions based on conclusions made by neural networks. Requirements for competencies in specific areas will decrease, while requirements for speed of work will increase. This is already noticeable now — people’s work is being massively transferred to automation through neural networks. The argument is simple — business metrics are growing, so it works. Only those who can apply neural networks in their work will survive here.
Career growth
Completing my studies will give me the opportunity to focus more time and attention on things that are useful and interesting to me. I already have a job, so the next question is: how can I grow up? There are two main areas: actual work and work-related activities.
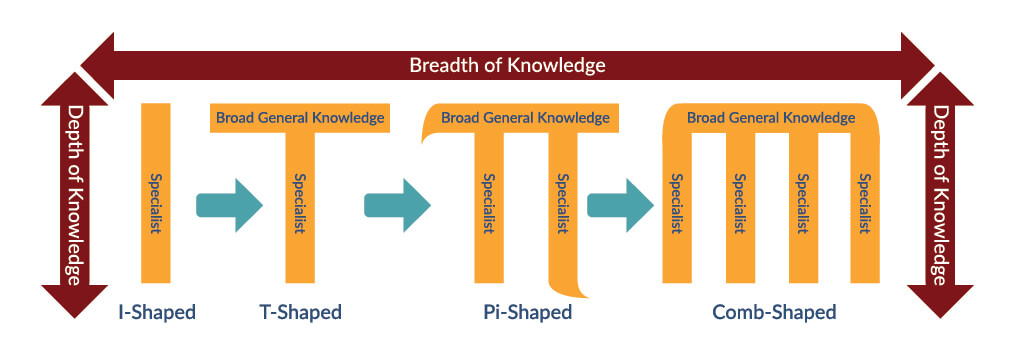
Cool projects, research, and certifications develop a specialist “in depth”. But as I grow in my position, I begin to see the need to expand my competencies “in breadth”.
This idea is to grow from an I-shaped specialist to a T-shaped specialist according to the Shaped Competencies model. In short, “depth” knowledge is our technical specialization, 80% of our competencies. And there is “broad” knowledge — related areas that are also necessary for our work, 20% of our competencies. For example, for a developer, development skills are “in-depth,” while analytics and testing skills are “broad.” You can read more about this in D. Blinov’s blog.
Projects, research, and certifications
Basically, it’s about work or growing your skills “in depth”. There are a few ways to do this: working (projects), studying something (research), and taking courses (certifications).
In terms of work, it seems that I have learned how to do penetration testing. I am capable of conducting complex penetration testing projects (external/internal networks, web/mobile applications, social engineering, etc.), covering everything from pre-sales and technical implementation to reporting and presenting project results.
The next stage for me is Red Teaming. I need to learn how to gain initial access, consolidate it, and move laterally within the customer’s infrastructure, taking into account the customer’s existing security and monitoring measures. This includes developing my own tools and payloads, execute social engineering and physical intrusion.
I know how to do each of these components separately. Now I need to put everything together into a single puzzle and put it into practice. Next is studying various tactics, techniques, and procedures (TTPs). I need to be able to implement them to test their coverage by the customer (Purple Teaming). It’s difficult, but interesting.
Working as a pentester involves a lot of constant research. This means that it is essential to keep up with the news, current research, and conduct research yourself. The goal is to stay relevant and improve the quantity and quality of provided checks during the pentest. Main research topics:
- Current attacks and vulnerabilities;
- New technologies (e.g., cloud and AI);
- Fundamental technologies (low-level programming and hardware).
Here, I usually look at current needs. If I come across something interesting in a project, it’s time to do some research. If there is nothing like that, I open my backlog and take something to work on.
As for certifications, I stopped “taking everything in a row”. After passing OSCP, I realized that I already had the foundation for a junior-middle pentester. Now I need to go deeper, and broad courses on everything are no longer suitable for me. If I take any new courses, they will be specialized in a specific domain, such as malware development (MalDev) or cloud infrastructure (Cloud Security). In general, I am now looking for useful knowledge to better solve current problems and master new ones.
Related competencies and management
My in-depth knowledge is penetration testing. Now I need to identify related areas for development. For the near future, I have identified the following domains for broad development:
- Copywriting. To improve the quality of my reports, which are the main product for the customer;
- AI. The ability to use various AI tools allows me to solve problems more effectively, including those that I cannot solve myself;
- DevSecOps. Knowledge of secure development and DevOps helps automate my tasks (see DevOps for Red Team Initial Access Operations) ;
- Architecture security. Understanding “target secure architecture” helps me give better recommendations for improving customers’ information security processes and infrastructure (see Secure Network Architecture);
- Management. Managing a team to scale my activities and cover areas in which I do not have the necessary expertise. More on this below.
At some point, I also want to try myself at management. For me, management is about building systems that perform a certain function. These systems consist of people, processes, and technologies, the combination of which produces results.
Right now, my maximum is a team of five people focused on one area of work. Next, I want to move to the next level of abstraction — managing teams, taking responsibility for an entire department consisting of several divisions. In general, I want to move from the tactical level to the strategic level. To do this, I am working on detailed mind maps of the organizational structure and processes.
The main problem is controlling execution without creating useless detailed reports. It is difficult to find a balance between the quantity and quality of “give me a status” requests. I am slowly looking for solutions.
Going to international level
I’ve always been curious about what’s out there, beyond the horizon. Basically, most of our lives are about picking up ideas, tools, and trends that come from the West. And it’s not just everyday life — it’s the same at work. A specific example is penetration testing: when Black Hat USA 20XX and DEFCON XX take place, and everyone eagerly processes, adopts, and continues working. And so it goes until the next year.
Of course, one could argue about penetration testing specifically — there are talented researchers in the CIS area, and some things appear here first. But the numbers still say: 90% from there and 10% from here.
Because of this, I’ve always been curious, what’s it like to be first? What’s it like to be among those who are creating the future? In a highly competitive environment, not for repeating something already known, but for creating something new?
This interest has never faded in me. I want to find out. I want to be on par with the best. And that’s why I think I’ll soon begin my journey to the West.
Products vs Services
Having worked in consulting for several years, I strive to improve my knowledge, the complexity of the tasks I solve, and my position every year. Because of this, I am getting closer and closer to “business”. In this case, I mean that I am beginning to see and understand the value of different types of work “in money” and their profitability for the contractor, respectively.
Provision of services - 20-30 percent margin in developed markets. There are undeveloped markets in the CIS where you can charge for 100% or more, but it is only a matter of time before they are flooded with mediocre contractors who will dump prices due to low quality services. This will create competition and reduce revenues. But the main problem here is the business model. You cannot provide services on a continuous basis, on a subscription basis. You cannot “hook” a client on your services. Each consulting project is a one-time job, a single project. You may have regular clients, but this is only until the client wants to “close the issue on their own”.
Product development and sales - 100 percent and higher margin in any market. It is essentially impossible to assess the value of “intellectual property”, so the price tag can be anything. In addition to this, the business models of all vendors have shifted to a “one-year license” or a more sophisticated formulas. Products are no longer sold on a one-time basis, everyone is hooked on a subscription to generate a regular and predictable cash flow.
Moreover, now you can find niches where your product has to “do something” related to the topic — and you’re already doing well. From personal experience, I have seen many times how another vendor takes semgrep, adds a login form and dashboard to it — and there you have SAST, costing you 50-100 thousand of dollars. The margins are huge. And there’s nothing we can do about it yet — there are very few specialists on the customer side who really understand the area and can determine that the product is bad and won’t deliver the promised benefits.
In general, if you think long-term, you won’t get very far with services. Because of this, I think that “being a pentester for life” (or insert any consulting job here) is a bad idea. Your active work will end someday and is impossible without you. Your product will always work without you.
My own business
The previous section was a smooth transition to the idea of starting my own business, working for myself. Having worked in both startups and corporations, I began to understand who earns money, how, and from whom. I increasingly ask myself: why do I work?
The answer is simple: I need money.
If it weren’t for the urgent need for money, I wouldn’t work for someone else. Year after year, I come to this conclusion more and more often. Let me explain why.
Let me start by saying that I really like what I do. I want to continue, I want to get better and be useful. But as my skills grow, the disadvantages of working “for someone else” begin to outweigh the advantages.
What are the advantages of working for someone else? - Stability and focus. By stability, I mean a predictable income with a near-zero chance of loss. For me, focus means the ability to do only what I specialize in and refuse to do “work that isn’t mine”, shifting responsibility to colleagues or someone else.
Now for the cons. Overall, there is only one con — I am prevented from working. More specifically, there are three main drawbacks: established processes, approvals, and the absence of risk compensation.
By established processes, I mean the need to adapt to other people’s processes that were developed 5-10 years ago and are completely ineffective in the current reality. Examples include equipment procurement processes, contract approvals, and non-digitized document management. Have you ever bought four laptops in six months? I have.
The image below says: “You cannot simply take a contract and send it for approval. You need to agree on a memo to initiate the contract approval process.”
Approvals can also be considered as bad established processes, but I want to highlight them separately, as they cause a significant amount of work to be delayed for a considerable amount of time. There are several issues with approvals, which are discussed below.
The first is that I have to coordinate with people who don’t understand what I’m doing. It’s very difficult to explain what needs to be done and why. In this case, either you have a good relationship with a colleague who has influence over the approver, or be prepared for a lot of meetings to discuss the need of discussing your project.
The second is that if your approval chain consists of more than two people, your project is dead. If you show initiative “from below”, be prepared for a lot of obstacles. The approvers will pass you from one to another, because since the initiative did not come from the top, why get involved? No one will even bother to figure out what you want to do. The solution to this situation may be to go to the top management of the organization, explain the situation, and ask for help in pushing the initiative through.
The third consequence follows from the first two. I don’t want to discuss this. I want to do it. I know how and when it should be done. Why should I wait for something or someone useless in my work? It is clear that by staying in your current job, you seem to agree with these rules, but for how long?
The last problem is the price of risk. I don’t get as much as I could if I took full responsibility for everything. In essence, this is a consequence of working as an employee — you perform a certain function, and your potential earnings are capped, often without the possibility of pushing those boundaries. And this immediately raises the question: why should I do more, better, or higher quality work? Why should I show initiative? Why should I try to take on related functions? After all, I won’t get anything for the risk of failure, I won’t get more for the quantity or quality of my work.
Some companies are able to solve this problem through KPIs and bonuses. But the problem with any KPI is that the employee fills in the numbers for a specific metric, rather than bringing real value. KPIs work well in assembly line work, but they don’t work at all in intellectual work. To solve this issue, there is a concept called objectives and key results (OKR), which proposes iteratively reviewing KPIs every quarter. The idea is great, but very few companies have been able to implement it in practice, mainly giants like Google.
I began to feel these problems most strongly in a corporation-type company, where there are many people, established processes, and managers of managers. In such complex systems, solving even a small task for half a day can easily turn into weeks of discussion and then months of coordination. In small companies, it’s much easier, and you really have the opportunity to do something good quickly and without the involvement of useless people and processes.
All these problems are leading me more and more to the conclusion that I should start working for myself. I want to do things that interest me and that benefit people and the world around me. And I want to earn money from it if I succeed, and lose money if I fail. Without managers, coordinators, and intermediaries getting in the way of my goals.
I want to win.
Conclusion
That’s all for today. Thank you for taking the time to listen to my experiences and thoughts. I hope this experience will help someone understand what they need and help them move in the right direction.
Thank you for reading, I hope it was useful for you ❤️